center for long-term cybersecurity | cybersecurity | Design tools & EducationDeveloping Product Design Tools for Cybersecurity
UX Researcher | 2017 - 2019
How might we consider cybersecurity vulnerabilities in the product design process?
techniques & toolsDesign: Literature Review, Trend Analysis, User Interviews, Surveys, Data-driven Personas, Whiteboarding, 2x2 Matrixes, User Quadrants
Tools: Amazon MTurk
TeamAdvisors: Dr. A. Agogino, Dr. E. Kim, Dr. J. Yoon
UX: J. Kwon, T. Liaw
Final ProductChallenge
Cybersecurity is a rising threat in current society as more products and services become connected to the Internet. Cyber crime damages are predicted to reach $6 trillion annually by 2021. Although current efforts to prevent these crimes include technology and governmental interventions, such as the General Data Protection Regulation (GDPR), there are no effective methods addressing user interventions. In previous research, we discovered that product designers do not consider cybersecurity as a design factor.
ObjectiveDefine the vulnerabilities and trends regarding cybersecurity.
Identify consumer groups and behavior regarding online actions and cybersecurity awareness.
Create intervention methods to address cybersecurity in product design to reduce cyber crimes that can prove costly to companies and consumers.
User Research
Roadmap
To achieve our goals, we wanted to generate UX research tools, initially focusing on data-driven personas for product designers to emphasize with the users affected by cybersecurity.
To create these personas, we gathered data on user behaviors regarding their online behavior and awareness of cybersecurity by conducting:
Trend Analysis (N=23 articles)
User Interviews (N=20 Participants)
Surveys (N=188 Participants)
After creating personas based on the user research’s data, we created supplementary 2x2 Matrixes and User Quadrants to help designers frame their understanding of users.
Literature Review
We conducted a literature review to define the cybersecurity sector. I was in charge of:
Identifying industries that involve cybersecurity.
Mapping the industries’ risks and methods regarding protecting online consumer data.
Defining populations vulnerable to cyber crimes, including the elderly and parents with young children.
We found that precautions for cyber crimes existed on the regulatory and technological level, but no effective methods existed on the product design or user level.
Trend Analysis
We conducted a trend analysis with 23 articles based on cyber crimes.
Here we differentiated cybersecurity issues into two types:
Informational cybersecurity issues
Hardware cybersecurity issues
Cyber crimes on informational data occurred in 71.4% of the cases, while cyber attacks on hardware occurred in 28.6% of the cases. Although severity of the cyber crimes varied, the amount of people victimized in almost all information-related cases involved >1000 consumers. In hardware cases, affected consumers were typically <1000.
Based on these findings, we decided to narrow our efforts to focusing on users vulnerable to information cybersecurity cases.
User Interviews
I led the conduction of 20 user interviews to understand how users interact with smart devices and their cybersecurity awareness/behavior.
Guerilla Recruitment:
Public areas including cafés, airports or references from peers.
Question Focuses:
User perception on cybersecurity issues
Cyber attacks context
User response and concerns
User Interview Participant DemographicsUser Interview ResultsWe found a strong correlation of participants’ cybersecurity awareness and behavior with their ages.
Parents of Children
As we also wanted to understand the vulnerable population of parents with children, we found that 9 out of 10 participants with children were concerned about their children’s device usage and the inherent cyber risks, but only 2 out of those 9 participants actively monitored their children’s online behavior. The participant who was not concerned about their children and cyber crimes reasoned that they trusted that their children should already inherently know the risks of online behavior.
Initial Personas & FrameworksAfter conducting the literature review, trend analysis and user interviews, I created initial personas and related frameworks in order to direct the focus of the questionnaire for the surveys.
Whiteboard brainstorm of initial personas and frameworks
Surveys
188 surveys were conducted with Amazon MTurk, so data consisted of a randomized, large-group population in order to gain a large-scale understanding of the relationship between user characteristics and cybersecurity behavior.
Question Focuses:
Awareness of cybersecurity issues
Methods of using digital devices and services
Methods of responding to cybersecurity
Survey ResultsWe found that:
Users who share devices with others and are more proactive with protecting their online information have the highest self-perceived cybersecurity awareness and the lowest amount of experiences with cyber attacks.
Female users who share devices with others have the lowest self perceived cybersecurity awareness.
There is an inverse proportion between device use frequency and cyber attack experience.
UX Tools
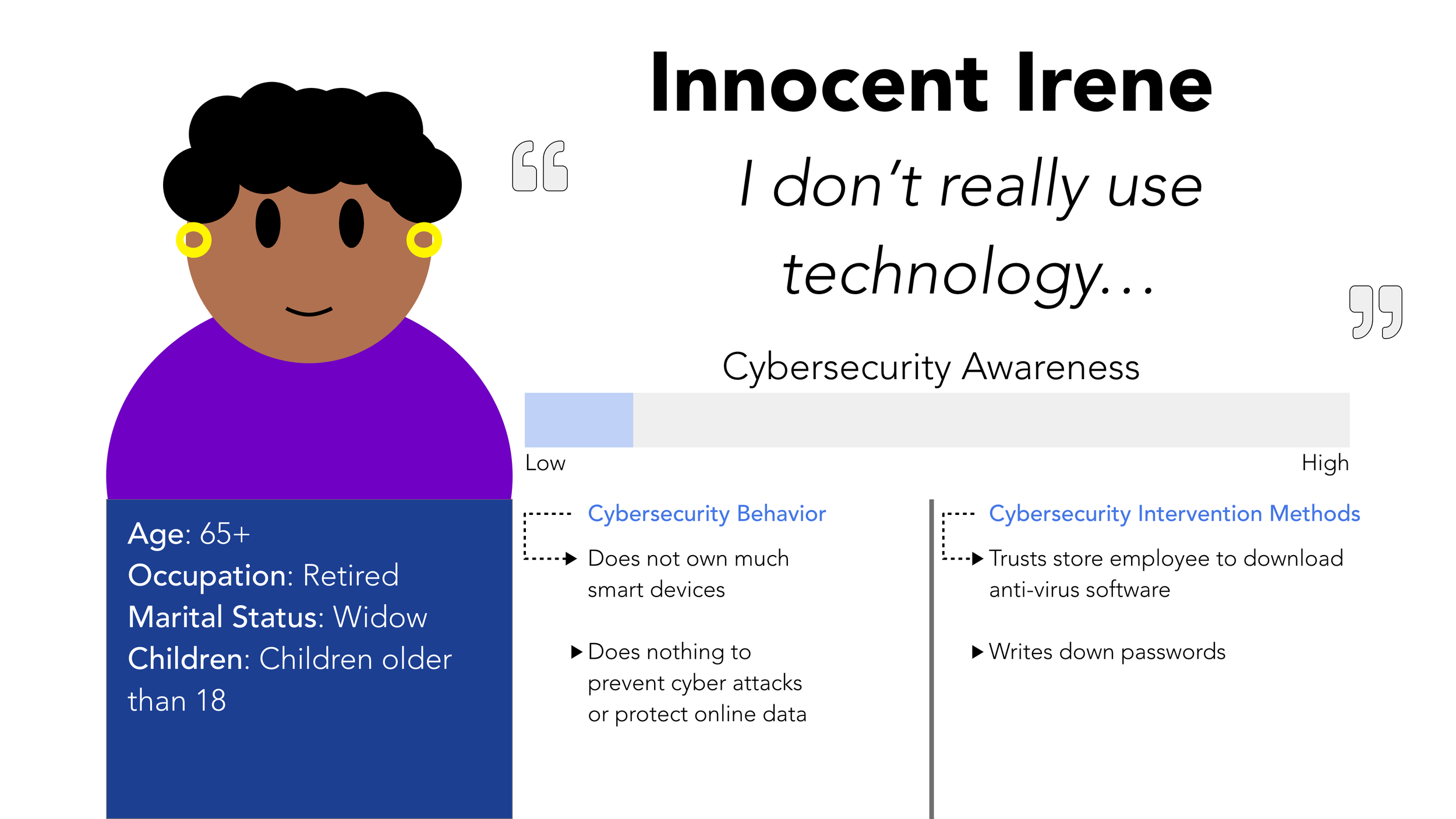
Personas
We came up with 8 personas after analyzing the data from the user research. Two of the personas are shown below.
Frameworks
We created two 2x2 matrixes and 8 user categories to help designers understand and conceptualize the personas. These matrixes focused on: user awareness and user control.
Impact
Our team submitted an academic paper at the Design Society: International Conference for Engineering Design which I presented at the conference in Delft, Netherlands. If you would like to see more information about the user research process or the personas/framework definitions, see our publication
This work led to the creation of design intervention cards, which were implemented in a course, Human-Centered Design Challenge: Making Mobile Sensing and Cybersecurity Tangible, at the University of California, Berkeley as tools for future UX designers.
International Conference on Engineering Design(2019) Presentation
Design for Cybersecurity Cards